How to identify and avoid 5 types of phishing tactics
With crypto prices rising, scam attempts are too. Social media accounts, emails, websites, and more are hacked or just impersonated in clever ways—various forms of "phishing"—all in pursuit of stealing your personal information and eventually your digital money. The good news is that protecting yourself and your crypto investments doesn't have to be hard: by knowing what to look out for, using common sense, and trusting your instincts, you'll stay one step ahead of bad actors. That's why Invity is here to fill you in on some of the most common phishing scams and how to avoid them.
What is phishing?
Phishing is the most common type of cybercrime. When we think of crimes in the physical world, most of us can picture a masked man with a knife or gun using intimidation or violence to take what they want by force. This type of cybercrime, however, is based on deception and persuading victims to willingly hand over money or sensitive information like passwords. You may hear the term "social engineering" in the context of phishing scams—this describes how cybercriminals use psychological manipulation to get people to do what they want. This is where the term "phishing" comes from: convincing bait is used to lure and manipulate humans into bad situations just like you might use a worm to hook a fish in a lake or river.
Most phishing attempts boil down to this basic definition, but their real power comes through the many different channels that cybercriminals use. These can make their attacks appear unique and even trustworthy, or they may just catch the average person off guard.
What is social media phishing?
Social media is a part of almost everyone's daily life, and it is particularly prominent in the crypto space. Major, influential Bitcoin personalities rely heavily on their personal Twitter—ahem, X—accounts to share their opinions and interact with the community, and crypto businesses use places like LinkedIn to share product updates and attract new customers and partners. Unfortunately, with the billions of different accounts out there and often little to no way to verify who is suspicious and who isn't. The simplest social media phishing technique is sending private messages, or DMs. Some random account may message you, for instance, promising to provide you with a certain number of new followers for the low, low price of €5 dollars, payable via credit card. Once an aspiring influencer has provided their credit card info, the charge turns out to be many, many times larger.
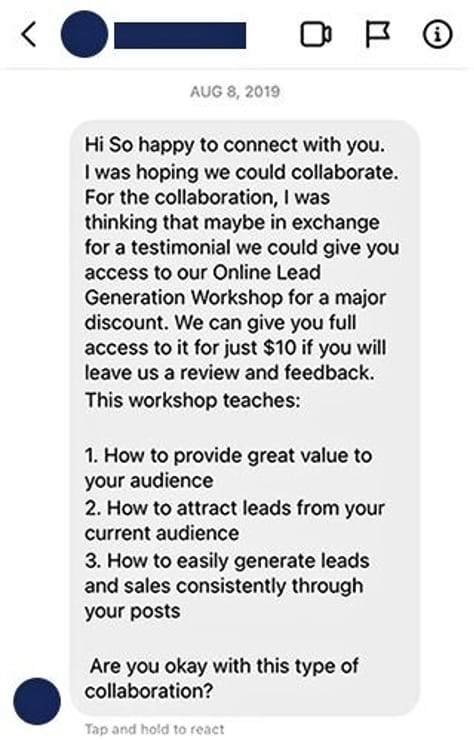
However, scammers might instead ask that you send a certain amount of Bitcoin and request your wallet details to make the deal. They rely on people who aren't familiar with crypto to share their seed and/or their wallet's private key; these aren't only unnecessary for making Bitcoin transactions, they give bad actors full access to your crypto funds. If there is one thing to take away from this article, it's that you should never share your seed or private key with anyone.
DMs like this can be automated and sent on a mass scale, making it cheap and easy to reach thousands of people instantly—fraudsters don't need a high success rate to make this profitable.
How to avoid social media phishing
Because social media is such a huge part of modern life, most of us have learned to ignore the large amount of spam we get daily. However, it's important to remember some basic online safety.
- Don't accept friend requests from people you don't know. If you're not familiar enough to recognize someone who is messaging you, there's probably not much good in connecting with them.
- Never share your seed, private key, or wallet app password with anyone. It bears repeating.
What is spear phishing?
There are also more sophisticated attackers out there who personalize their attacks; when a phishing attempt is targeted to a specific individual or organization, it's called spear phishing. With surprisingly little technical know-how, it's easy for an attacker to set up an account or a full website that looks strikingly similar to a legitimate social media account, social media platform, bank, or utility company. Bad actors usually set up these sites based on large amounts of leaked data such as the names, account numbers, and email addresses of actual customers—databases like these are widely available on the dark web. Fraudsters then send emails customized, often using your real name and other details, usually with claims that your account has seen unauthorized activity, you need to verify your details, or you need to take some other action fast.
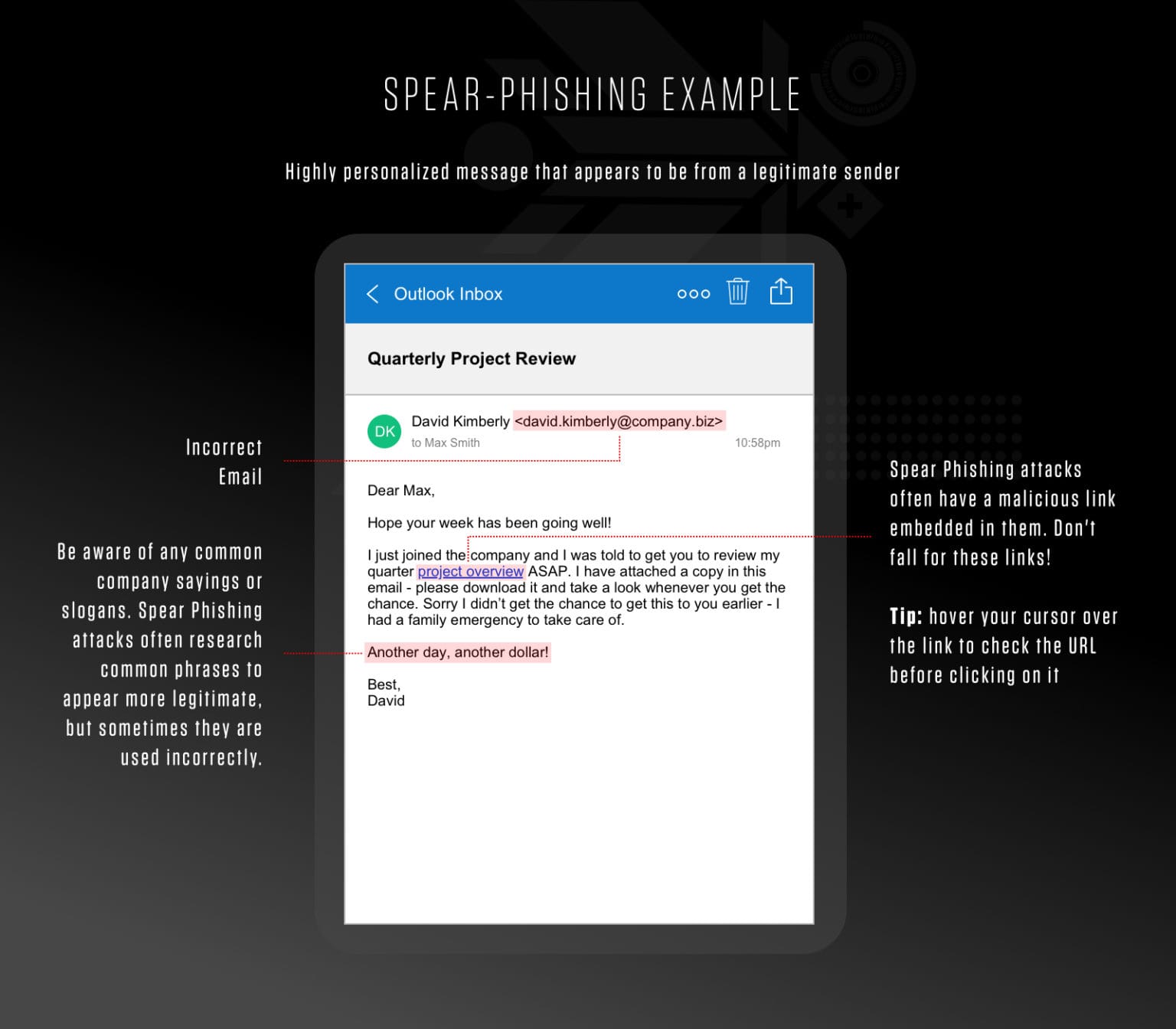
The message will usually contain a convincing-looking link that leads to a convincing-looking login page where you'll input your email and password. These, of course, are all fake, and once you've shared your details, the attackers will have access to your account, your private messages, and anywhere else that uses the same email and password combination. For many people, this can include passwords to crypto wallets and/or exchange accounts, putting your funds directly at risk.
How to avoid spear phishing
- Never blindly click on links requesting personal information. Legitimate businesses typically won't ask you to follow a link to verify your information, and will almost never do so via email or private messages; if you're not sure about something, consult the site's support pages before clicking a link or sharing your info.
- Carefully check the fine details. Fake email addresses and websites can be very similar to the real deal, but there are usually some giveaways like outdated logos, misspellings (for example, faecbook.com instead of facebook.com), or URLs that start with http instead of https.
- Use unique login details for each site. It's best to use different usernames and passwords everywhere; you can generate these and keep them organized in a secure password manager like Bitwarden or Proton Pass, both of which have excellent reputations and free versions.
What is whaling?
Dedicated attackers may be able to refine their targeting even more in pursuit of "whales"—high-profile victims and bigger paydays.
Particularly when scammers want access to a business or other organization's internal systems, it often doesn't take much detective work to identify who probably has access to those systems—these are often low-level employees but can just as easily be executives too. With a little research into online and even offline activities, digital con artists can gather plenty of information to fine-tune their messages and build relationships with their targets. With patience and persistence, hackers frequently gain unauthorized access to businesses, receive payments, or introduce malware to large-scale targets. Just this year, at least a dozen people close to the UK Parliament were involved in blackmail attempts that were highly personalized forms of spear phishing.
It's easy to think that the average person is immune to this kind of fraud—most of us aren't government ministers or CEOs, after all. Still, in today's increasingly digital world, it's easy to share more than we probably should about ourselves. If the wrong person pays attention and properly connects the dots, even a normal person's information can be used against them, resulting in a hefty profit for scammers.
How to avoid whaling
- Don't make yourself a target. If you're careful about the personal info you share publicly and don't reveal that you have large amounts of funds, then scammers are less likely to set their sights on you. Remember: it's good to talk about Bitcoin, just don't talk about your Bitcoin.
- Trust your gut. If something seems off or seems too good to be true—such as messages from someone you have no recollection of or an offer that promises fast, easy money—you're probably right. You shouldn't feel bad about not engaging.
What is smishing?
Smishing, or SMS phishing, usually uses similar techniques as large-scale phishing, spear phishing, and whaling. As the name suggests, though, these cybercrime attempts come through text messages on your phone. Bad actors will send spam text messages about special offers or even simple messages that look like verification codes, and will usually include a link for you to follow. The link, more often than not, will download malware or spyware to your phone. Even if you're careful about not willingly giving up your information, even simple malware like keystroke logging can provide your passwords or seed phrases to scammers.
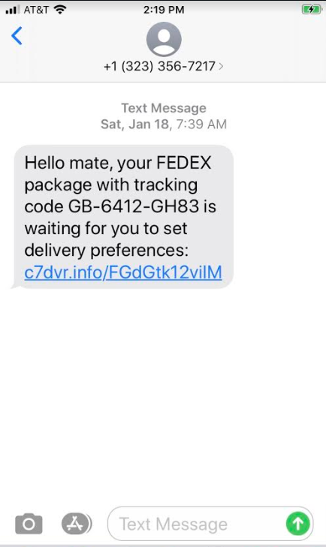
How to avoid smishing
- Don't respond to SMSs from unknown or suspicious numbers. Don't even message "STOP"—doing so will let scammers know your number is active and could add you to a spammer's list for further harassment.
- Keep your phone’s operating system up to date. This usually protects against the most common malwares hidden in smishing links.
What is vishing?
Vishing is a mash-up too—"voice phishing"— and it too comes over the phone: simply put: a scammer gives you a call. This may sound like an old-fashioned style of fraud, but it's stuck around because it's so effective. It's a favorite scam technique because it puts the target on the spot and manipulates emotions more forcefully than most other approaches on this list.
In this scam, not only are you talking to a real person, giving you little time to think through the situation and making you feel obligated to answer quickly, but cybercriminals also are very talented at creating high-pressure situations. Frequent scenarios include fraudsters posing as police, your country's tax authority, or as tech support for a device you recently purchased.
In each of these, the person on the other end of the phone will sound very official or even vaguely threatening—there's been an accident, you're at risk of an audit, or your computer has been hacked. They may even "verify" their authority using your actual information and claim that you need to take action immediately. The only way to clear your name, of course, is to truthfully answer the questions the caller asks, giving up your identity numbers, passwords, and more in the process.
How to avoid vishing
- Sign up to a do-not call list. Be very careful to give up your phone number only when absolutely needed, and add yours to a do not call list if your country has one. This isn't a surefire way to protect yourself, but it makes you a harder target to acquire.
- Don't give in to a sense of urgency. Don't let an authority figure pressure you into doing something right now—there are very few things that can't wait for at least a few minutes. Take a deep breath, think through the situation, and take a moment to consider if what they are saying is true or even plausible.
- Offer to call them back. Scammers often use "spoofing", or routing calls through numbers that appear legitimate but they don't actually control. If it's a real call about a real problem, the caller should be willing to let you hang up and return the call.
Trying to keep up with all the new scam tactics can seem like hard work at first, but getting in the habit of watching out for the scam tactics above can go a long way. If you already follow all of these steps, you can take your security to the next level with more tips on keeping yourself and your crypto safe and special steps to take to buy crypto safely. Most of all, remember that Invity will never reach out to you for any of your crypto-related info, making it not only the easiest but the most trustworthy crypto app out there—try it today!